Amazon S3 (Simple Storage Service) is a popular cloud storage service provided by Amazon Web Services (AWS). It allows users to store and retrieve any amount of data, at any time and from anywhere on the web. S3 buckets are the basic unit of storage in S3, and they can contain an unlimited number of objects. In this blog, we will discuss S3 bucket object ownership and its significance.
In Amazon S3, objects are owned by the AWS account that was used to upload the object to a bucket. By default, the owner of a bucket has full control over the bucket, and every objects (i.e., a files) stored in a bucket. Including the ability to delete it and modify its access controls. Moreover, the owner of a bucket can grant other AWS accounts or users permission to access and manage the objects in the bucket.
This is important because it allows the owner to manage the security of their objects and ensure that only authorized users have access to them.
For example, consider a scenario where an AWS user named Alice has an S3 bucket called "unique-bucket-name" and she has stored several objects in it. Alice is the owner of these objects, so she has the ability to manage their access controls, delete them, and take other actions as needed when she is logged in into AWS Console using her Access. If another AWS user named Bob tries to access one of Alice's objects without permission, Alice can use the access controls on the object to prevent Bob from accessing it.
Controlling ownership of objects and disabling ACLs for your bucket
ACLs Disabled (Recommended)
When ACLs are disabled and bucket owner enforcement is enabled (which is recommended), the bucket owner automatically becomes the owner of every object in the bucket and has full control over them.
With this setting, ACLs no longer determine access control for data in the S3 bucket. Access control policies are used instead to define who can access the bucket and its contents.
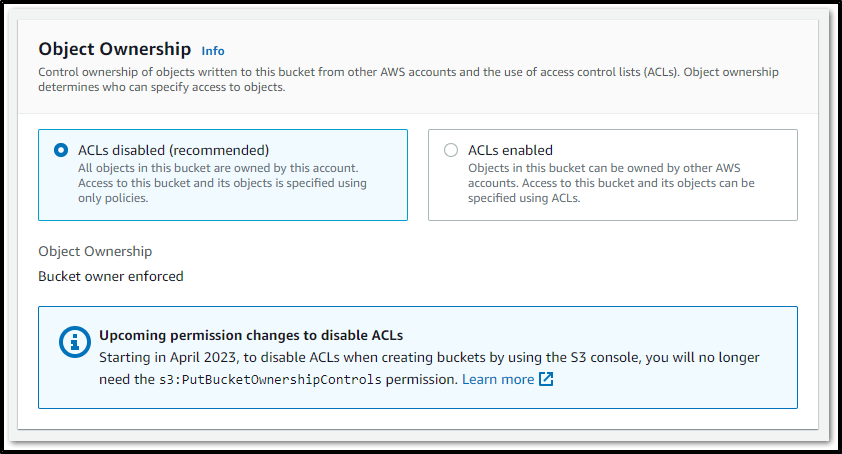
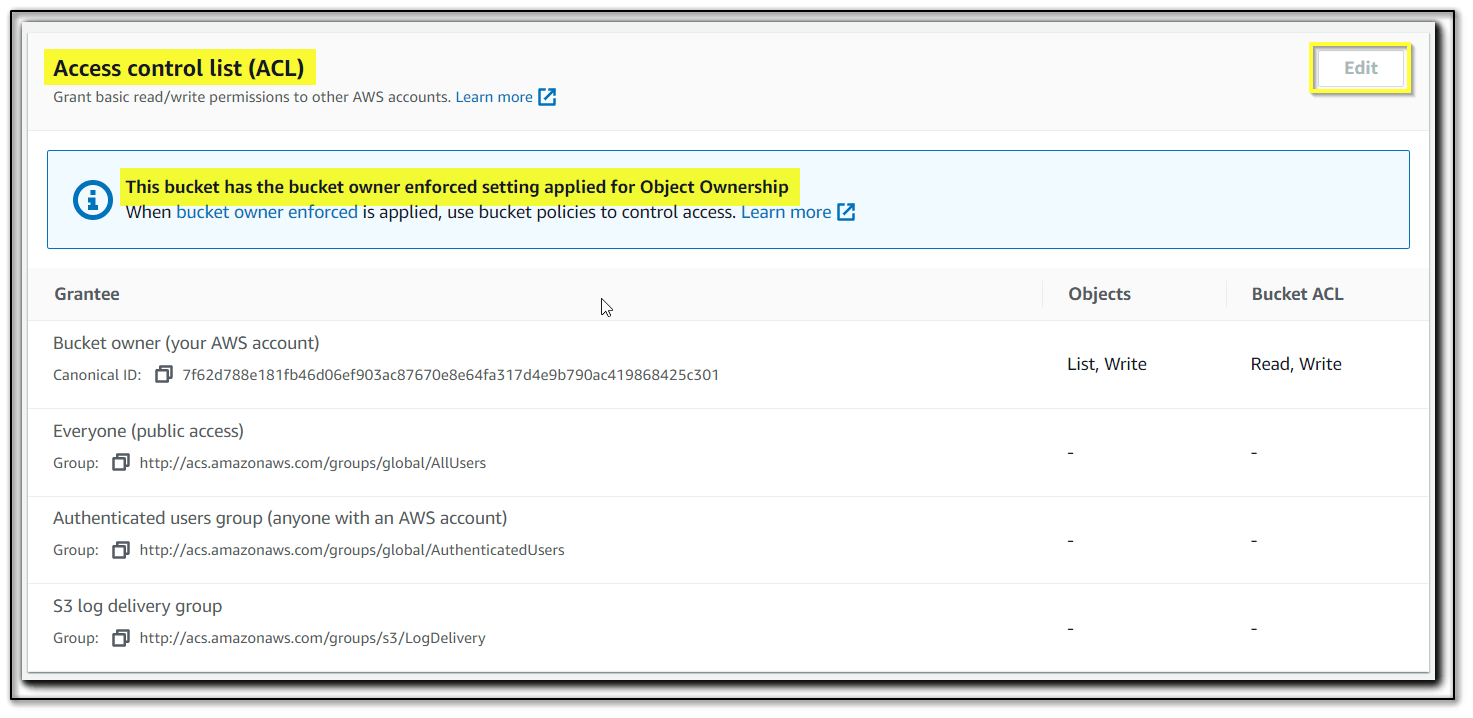
ACL is disabled. Object Ownership is handled by Bucket Policies. "Edit" Grayed out.
How Bucket Policy work? (Important)
Amazon S3 offers two types of policies, bucket, and user policies, which allow or deny permissions to different resources. A policy consists of the following elements,
Resources – Resources refer to the Amazon S3 entities to that permissions can be granted or denied to. i.e. Buckets, objects, access points, and jobs
Actions – Actions are the operations that can be performed on Amazon S3 resources. allow or deny.
Effect – Effect determines whether a user is allowed or denied the action requested. If you do not explicitly grant access to (allow) a resource, access is implicitly denied.
Principal – Principal is the entity or user that is being granted or denied permission to access the resources or perform the actions.
Condition – Conditions specify the circumstances under which the policy is in effect and can be used to restrict access based on factors such as time or IP address.
For example, The following example bucket policy allows Dave, a user in account Account-ID, s3:GetObject, s3:GetBucketLocation, and s3:ListBucket Amazon S3 permissions on the awsexamplebucket1 bucket.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Only allow writes to my bucket with bucket owner full control",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::111122223333:user/ExampleUser"
]
},
"Action": [
"s3:PutObject"
],
"Resource": "arn:aws:s3:::DOC-EXAMPLE-BUCKET/*",
"Condition": {
"StringEquals": {
"s3:x-amz-acl": "bucket-owner-full-control"
}
}
}
]
}
ACLs enabled
Bucket owner preferred – The bucket owner owns and has full control over new objects that other accounts write to the bucket with the
bucket-owner-full-controlcanned ACL.Object writer (default) – The AWS account that uploads an object owns the object, has full control over it, and can grant other users access to it through ACLs.
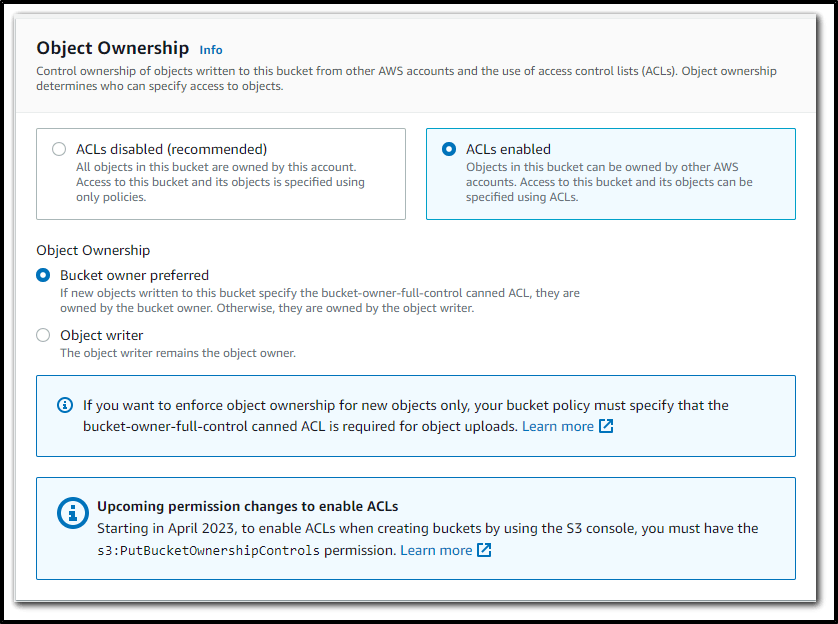
Object Ownership - Bucket Owner Preferred with ACL Enabled
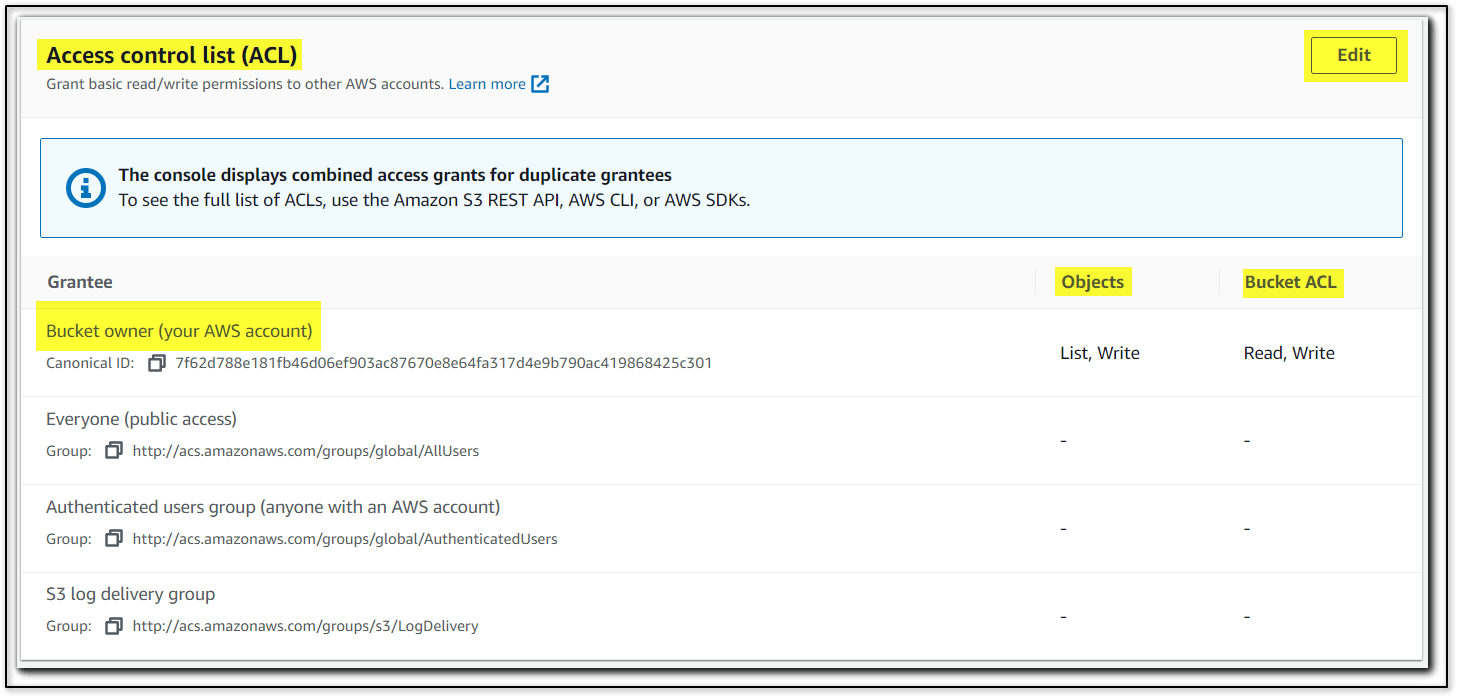
Object Ownership - Object Writer with ACL Enabled

This represents How editing ACL for list/read/write as per the requirement for Objects and Bucket ACL settings and enforce to related grantees for access Including other AWS Account.
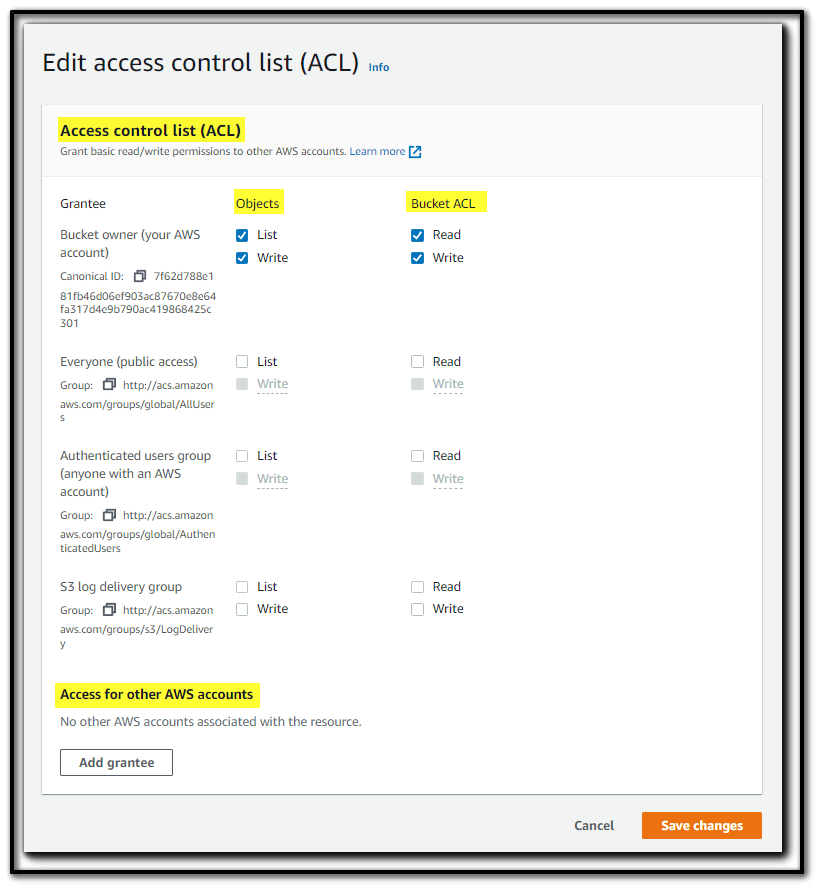
Requiring the bucket-owner-full-control canned ACL for Amazon S3 PUT operations (in Object ownership - bucket owner preferred)
When you enable the bucket owner preferred setting for Object Ownership, Bucket Owner have full control over the new objects that other accounts write to your bucket. If they use the "bucket-owner-full-control" canned ACL, you will be the owner of those objects. But, if they don't use this canned ACL, they will still have full control access. To prevent this, you can create a bucket policy that only allows writes with the "bucket-owner-full-control" canned ACL.
Example,
The following bucket policy specifies that account 111122223333 can upload objects to DOC-EXAMPLE-BUCKET only when the object's ACL is set to bucket-owner-full-control. Be sure to replace 111122223333 with your account and DOC-EXAMPLE-BUCKET with the name of your bucket.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Only allow writes to my bucket with bucket owner full control",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::111122223333:user/ExampleUser"
]
},
"Action": [
"s3:PutObject"
],
"Resource": "arn:aws:s3:::DOC-EXAMPLE-BUCKET/*",
"Condition": {
"StringEquals": {
"s3:x-amz-acl": "bucket-owner-full-control"
}
}
}
]
}
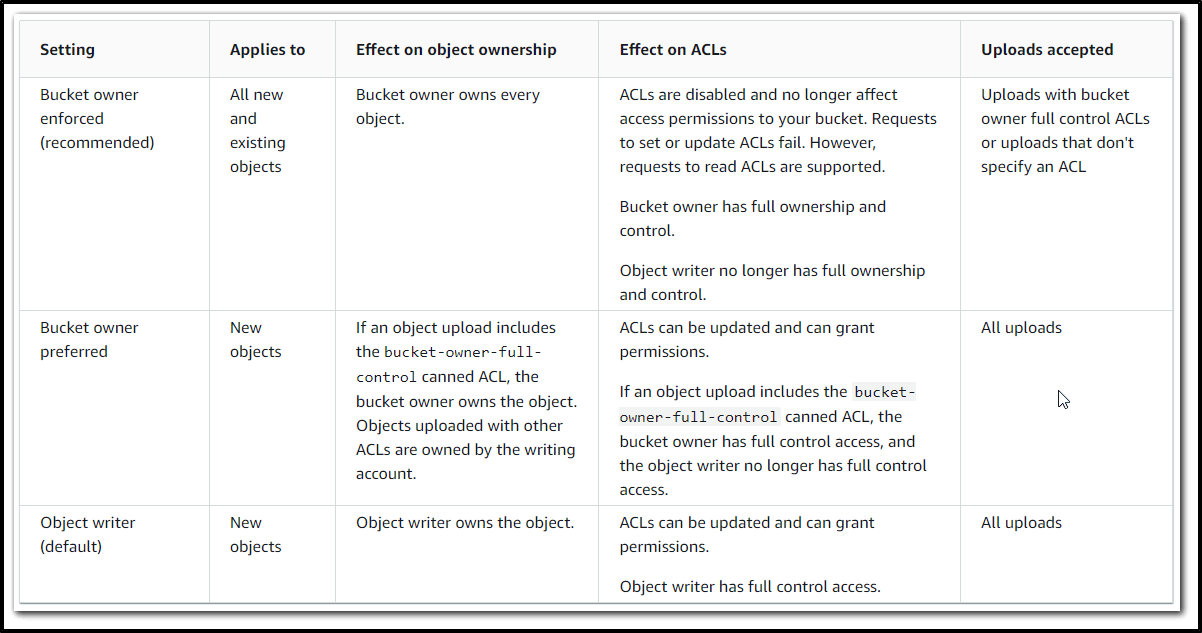
This table shows the impact that each Object Ownership setting has on ACLs, objects, object ownership, and object uploads.
If you use S3 Versioning, the bucket owner owns and has full control over all object versions in your bucket. Applying the bucket owner enforced setting does not add a new version of an object.
Example, Using the AWS Command Line Interface (AWS CLI) s3api put-object operation includes the bucket-owner-full-control canned ACL, the object can be uploaded to a bucket with disabled ACLs.
aws s3api put-object --bucket DOC-EXAMPLE-BUCKET --key key-name --body path-to-file --acl bucket-owner-full-control
Changes introduced by disabling ACLs
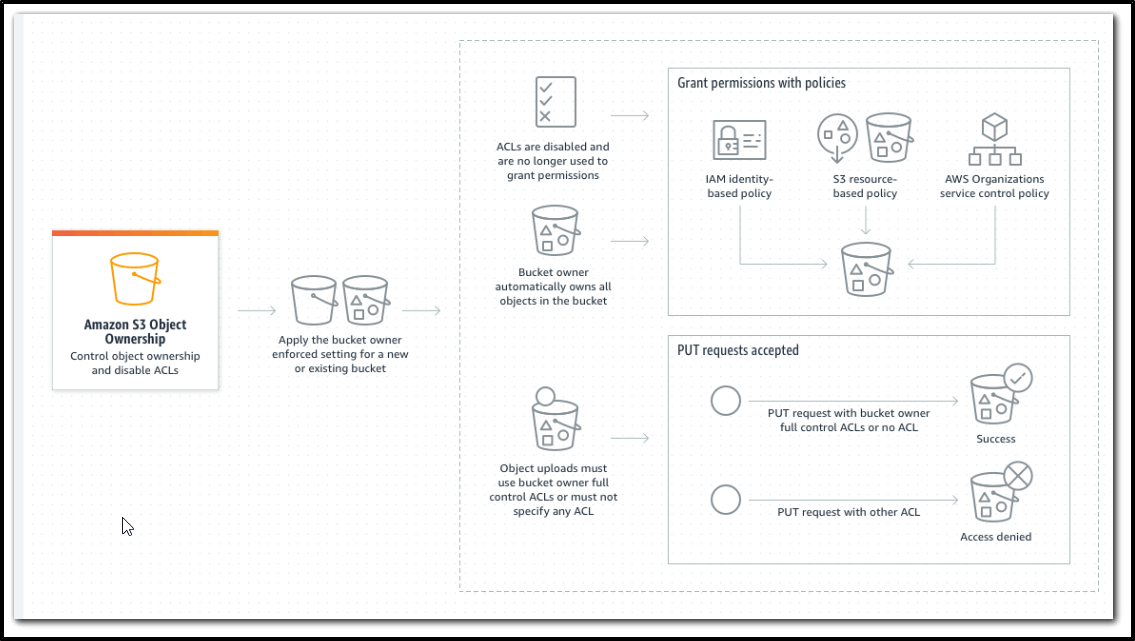
References to learn more,
Controlling ownership of Objects and Disabling ACLs for your bucket.
Disabling CLs for all new Buckets and enforcing Object Ownership.
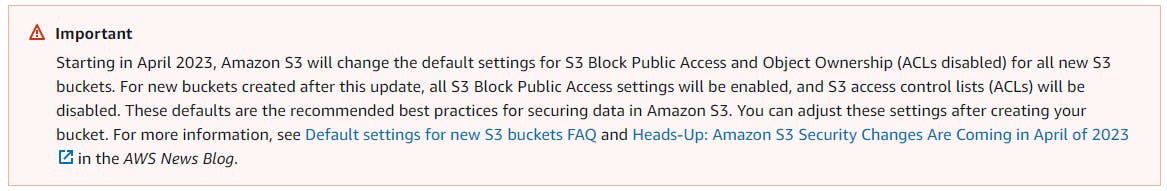
Heads-Up: Amazon S3 Security Changes Are Coming in April of 2023
Upcoming changes starting April 2023
"Bucket owner enforced setting" will be enabled for newly created buckets, making bucket ACLs and object ACLs ineffective, and ensuring that the bucket owner is the object owner no matter who uploads the object."
A subsequent attempt to set a bucket policy or an access point policy that grants public access will be rejected with a 403 Access Denied error.
"S3 Block Public Access" – All four of the bucket-level settings will be enabled for newly created buckets.
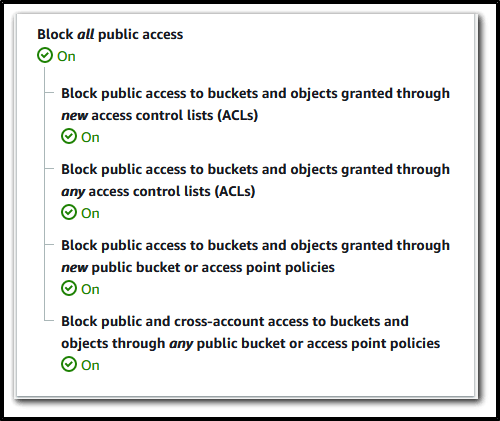
The Bucket owner-enforced setting will soon be enabled, which means that bucket and object ACLs will no longer be effective. This change is intended to ensure that the bucket owner is always the object owner, regardless of who uploads the object. If you wish to enable ACLs for a bucket, you will need to set the ObjectOwnership parameter to ObjectWriter in your CreateBucket request or call DeleteBucketOwnershipControls after creating the bucket. Please note that s3:PutBucketOwnershipControls permission will be required in order to use the parameter or function.

I hope this blog provides an understanding of S3 Bucket Ownership, along with practical examples and screen capture references, to help you gain a better understanding of the topic. Also, some references to read and learn more.
Thank you for the read. Hope you like it. I appreciate your time.
Follow for more Azure and AWS Content. Happy Learning!
Regards,

