Introduction
Amazon S3 (Simple Storage Service) is a cloud storage service provided by Amazon Web Services (AWS). S3 buckets are used to store and manage data in the cloud. S3 provides a simple and highly scalable way to store and retrieve large amounts of data from anywhere on the internet. This makes it a useful service for a wide range of applications, including data storage, backup and recovery, and disaster recovery.
S3 bucket security is very important for sensitive and confidential data stored in those storage buckets. Securing the data stored in S3 buckets from unauthorized access, accidental deletion, and other potential threats. Therefore, it is essential to ensure that the data stored in S3 is properly secured to protect against unauthorized access and other potential security risks.
Tips for securing your S3 buckets
Enable versioning to keep track of changes to your data
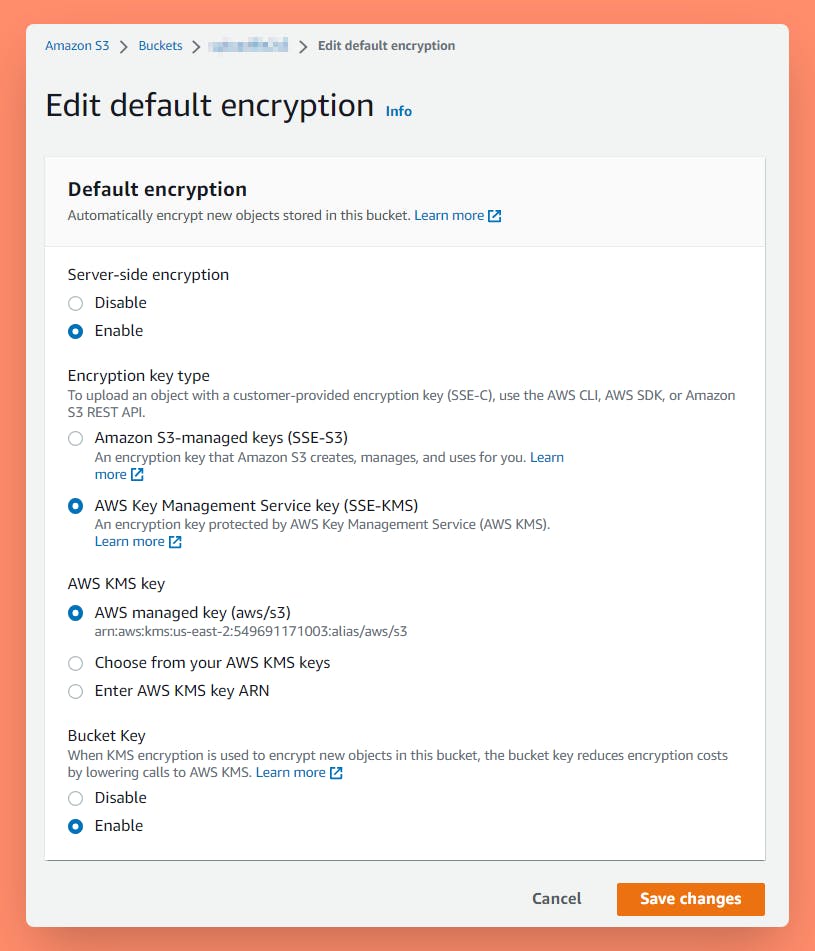
Use encryption to protect your data while in transit and at rest
Server-Side Encryption – Request Amazon S3 to encrypt your object before saving it on disks in its data centers and then decrypt it when you download the objects.
- To configure server-side encryption, see Specifying server-side encryption with AWS KMS (SSE-KMS) or Specifying Amazon S3 encryption.
Client-Side Encryption – Encrypt data client-side and upload the encrypted data to Amazon S3. In this case, you manage the encryption process, the encryption keys, and related tools.
To configure client-side encryption, see Protecting data using client-side encryption.
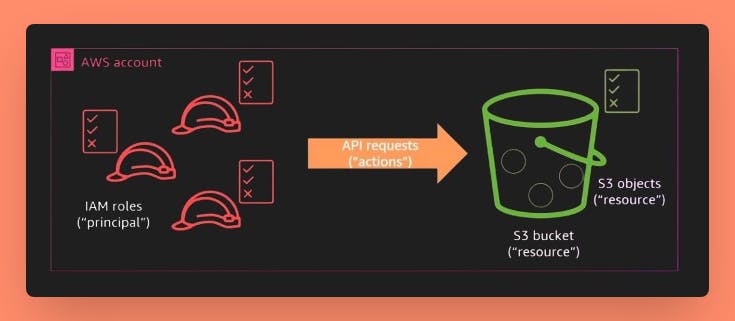
Limit access to your S3 buckets using Bucket policies and IAM policies
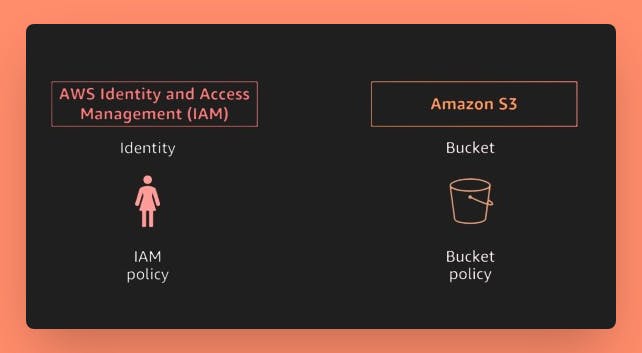
Bucket Policy
AWS has given an easy way to generate S3 Bucket Policy as shown here.
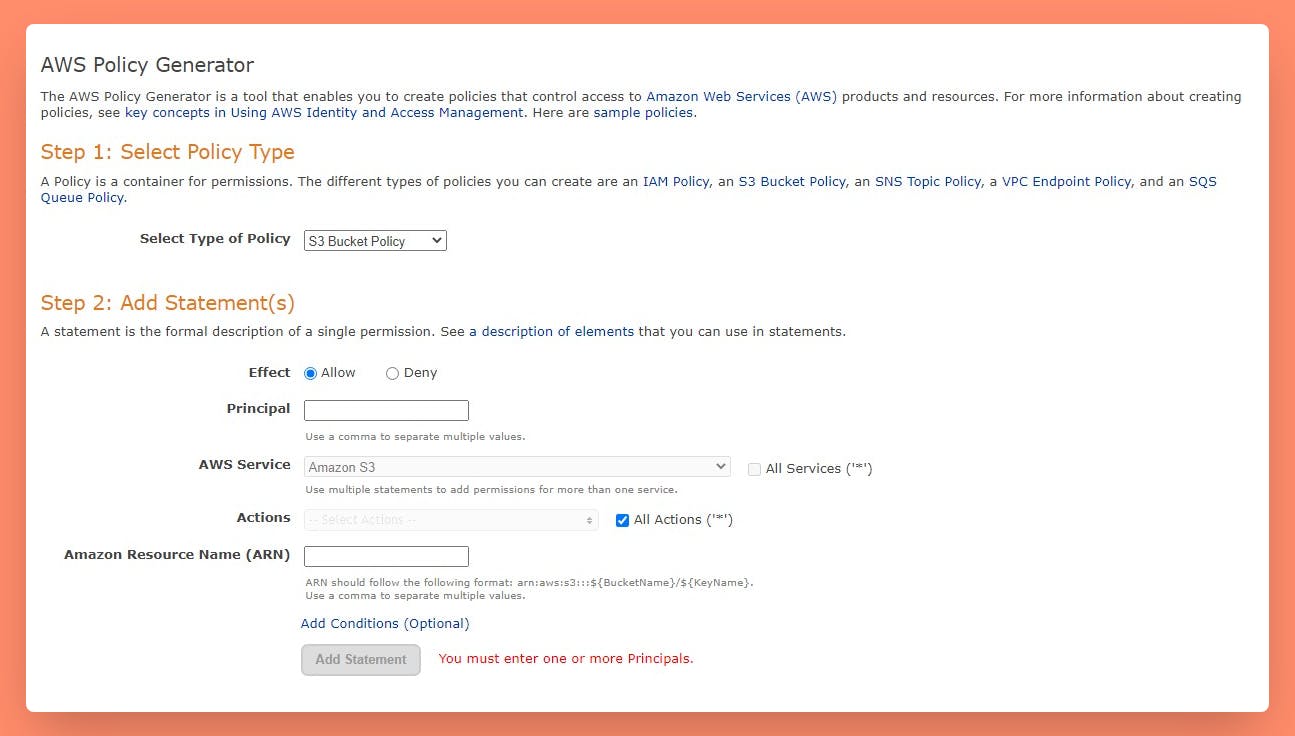
AWS Console > S3 > Select Bucket > Permissions > Bucket Policy > Edit
Sample Bucket Policy
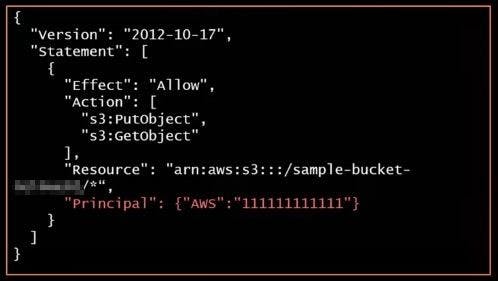
"Principles" > "Effect" > "Actions" > "Resource" : S3 Bucket / Object / *
Principles: Specifies whom the statement covers (Acc/Role/User/Srvs)
Effect: Specifies whether the policy results in "deny" or "allow"
Actions: Specifies the actions that is/are being denied or allowed.Resource: Specifies which AWS Resource the Policy Applies to. S3 Bucket
Now, this Bucket Policy can be applied to a Bucket as needed.
IAM Policy
/AWS Console > Security & Identity > IAM > Create Policy
Sample IAM Policy
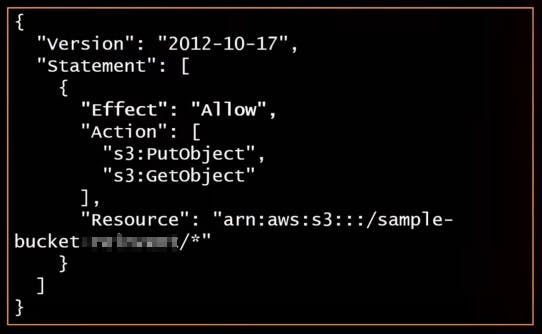
"Effect" -- > "Action" --> "Resource" : S3 Bucket / Object / * (all)
Effect: Specifies whether the policy results in "deny" or "allow"
Actions: Specifies the actions that is/are being denied or allowed.Resource: Specifies which AWS Resource the Policy Applies to. S3 Bucket / Object / *
Now, this IAM Policy can be applied to IAM User or IAM Role as needed.
Additionally, We can add a Condition element to these IAM/Bucket Policies
"Condition" : {
"{condition-operator}" : { "{condition-key}" : "{condition-value}" }}
"Condition": {
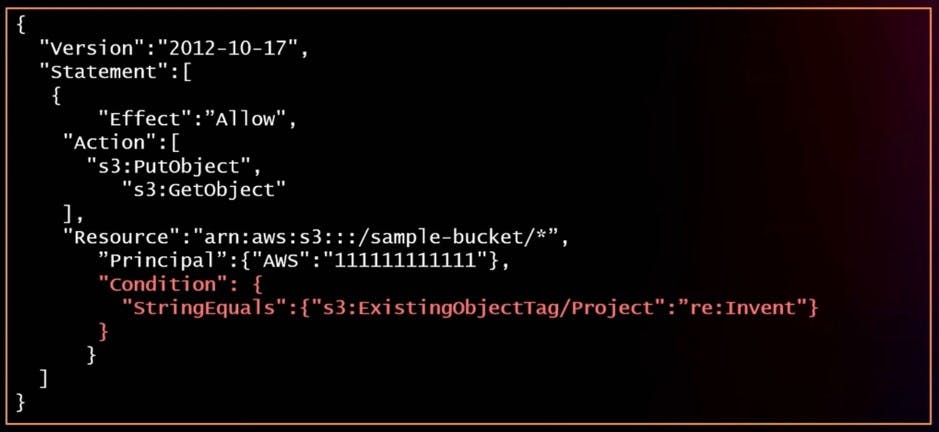
"StringEquals": {"aws:PrincipalTag/job-category": "iamuser-admin"}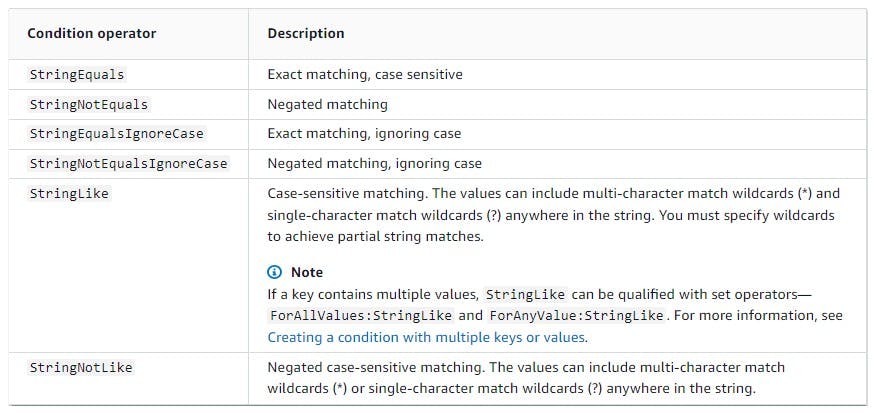
Policy Example with Condition :
AWS S3 Block Public Access
AWS applies protection by default against all accidental public access by Blocking all Public Access as a default setting while creating a Bucket.
This provides protection to permissions from ACL, Bucket Policy, or both.
At account Level
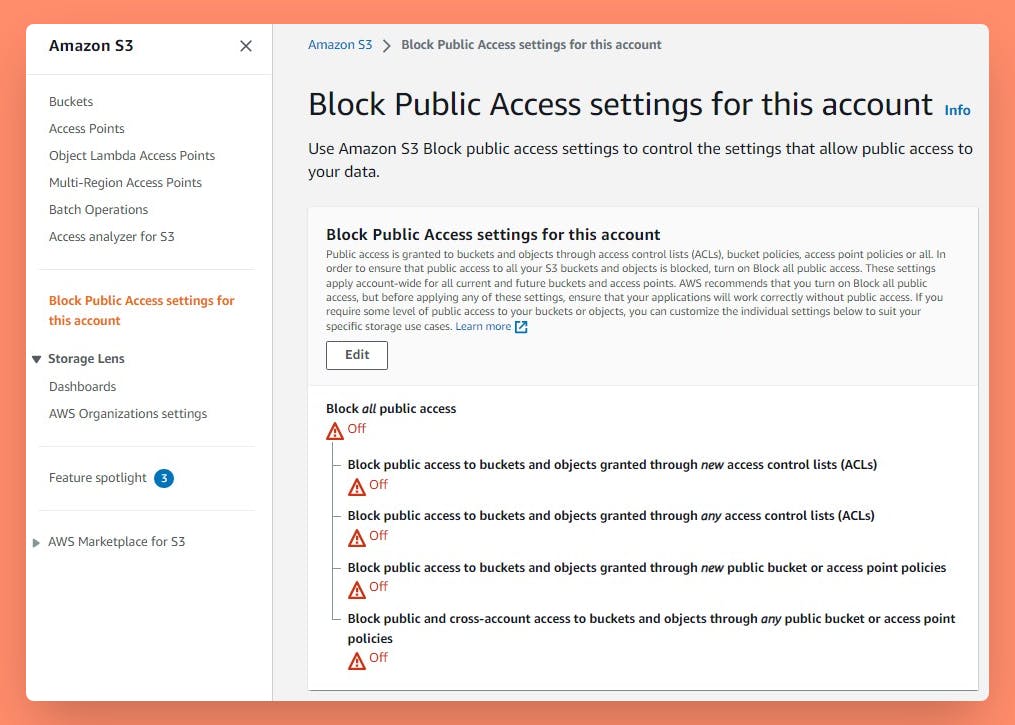
At Bucket Level:
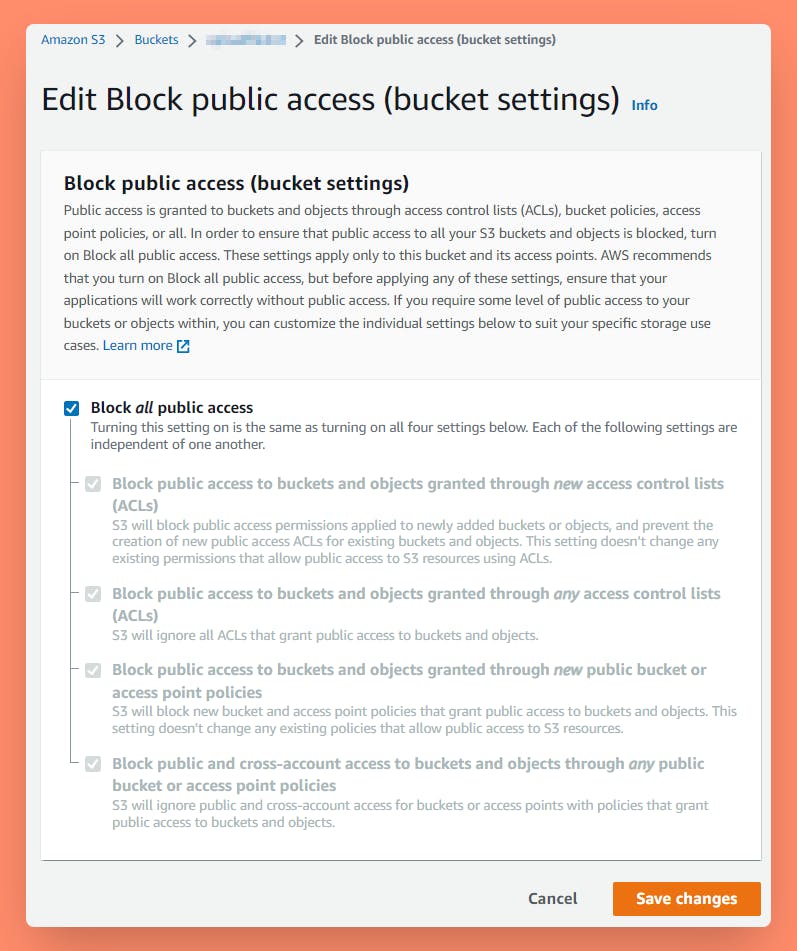
Monitor and audit access to your S3 buckets
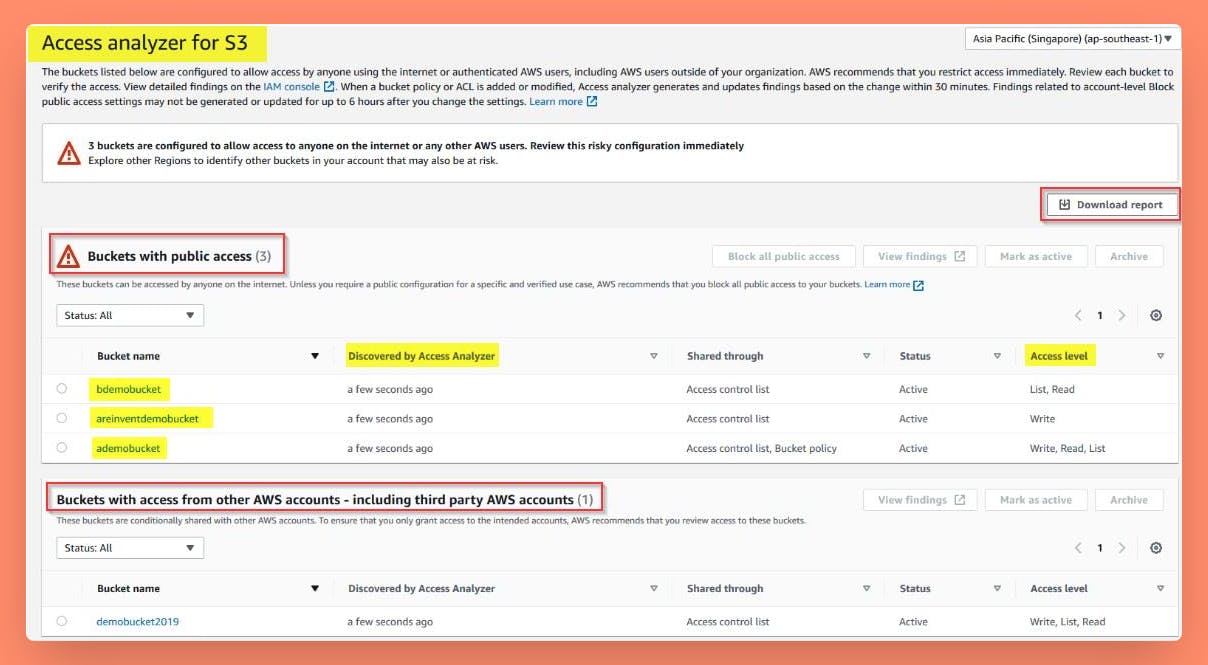
Access Analyzer for S3
It analyzes permissions for all Buckets in a particular AWS Region.
And Provides a Dashboard to show findings from public buckets and buckets shared with external users or accounts.
Access Analyzer reviews all Bucket Policies, Access Control Lists, Access Point Policy, and Block all Public Access Settings to produce findings.
Best practices for S3 bucket security
S3 Bucket Names are Globally UNIQUE (i.e. No two S3 buckets can have the same name Globally). Use unique and complex names for your S3 buckets to prevent unauthorized access.
To prevent Brut Force attacks and prevent Malicious Actor to find out your S3 Bucket Name, It is important to choose a name that is complex and not easily guessable to prevent unauthorized access to your bucket.
This means avoiding using simple names or common words, and instead using a combination of letters, numbers, and special characters to make the bucket name more difficult to guess.
Use multi-factor authentication for your AWS account to add an extra layer of security
Regularly review and update your IAM policies and bucket policies to ensure they are up to date.
Amazon S3 uses Identity and Access Management (IAM) policies and bucket policies to control access to your S3 buckets and the objects they contain. These policies specify who is allowed to access your S3 resources and what actions they are allowed to perform on them. It is important to regularly review and update these policies to ensure they are up to date and still reflect your desired access control settings.
For example, if you have added new users to your AWS account, you will need to update your IAM policies to grant them access to your S3 resources. Similarly, if you have changed the way your data is organized in S3, you may need to update your bucket policies to reflect the new structure. Regularly reviewing and updating your IAM and bucket policies will help ensure that only authorized users have access to your S3 resources and that they can only perform the actions you have explicitly allowed.
Use Amazon S3 ACLs to control access to specific objects in your S3 buckets
In addition to using IAM policies and bucket policies to control access to your Amazon S3 resources, you can also use Access Control Lists (ACLs) to fine-tune access to specific objects within your S3 buckets. An S3 ACL is a set of rules that define who can access an individual object and what actions they are allowed to perform on it.
For example, you could use an S3 ACL to allow certain users to read an object but not write to it, or to allow public access to an object while preventing delete operations. This allows you to have more granular control over access to your S3 objects, enabling you to fine-tune your security settings as needed.
You can ensure that only authorized users have access to your S3 objects and that they can only perform the actions you have explicitly allowed.
Keep Public Buckets in a Dedicated AWS Account.
- This will prevent any possibilities of public access to your S3 Bucket Data on Private Buckets by enabling "Block All Public Access" at AWS Account Level as it's in a separate AWS Account and Public Buckets are in a separate AWS Account.
Run and Review Access Analyzer for S3 to see any Access Vulnerabilities and Findings can be analyzed and corrected.
Use Encryption at Rest for each S3 Bucket in your Account.
Use Amazon S3-managed Keys (SSE-S3) - Free for all Buckets at least.
There are other Options for Encryption like "AWS KMS keys (SSE-KMS) with Customer Managed Keys" and "AWS KMS keys (SSE-KMS) with AWS Managed Key" to choose from.
Conclusion
There are several ways to secure an S3 bucket and the data it contains, including the following:
Use access control lists (ACLs) to specify which users and groups are allowed to access the bucket and the types of actions they can perform. This can help prevent unauthorized access to the bucket and its contents.
Enable versioning on the bucket to protect against accidental deletion or overwriting of objects. This allows you to recover previous versions of objects if they are deleted or modified.
Enable server-side encryption for the bucket to protect the data stored in it. This encrypts the data at rest, so that it cannot be read by unauthorized users.
Use Amazon S3 bucket policies to define additional security controls for the bucket, such as requiring SSL/TLS for all connections to the bucket or restricting access to the bucket based on the source IP address of the request.
Monitor and log access to the bucket to identify potential security issues and to track who is accessing the bucket and its contents. This can help you detect and respond to potential security threats.
By implementing these security measures, you can help protect your S3 bucket and the data it contains from unauthorized access and other potential security risks.
Thank you for reading and/or following along with the Blog.
Happy Learning.
Like and Follow for more Azure and AWS Content.
Regards,
Jineshkumar Patel

