EBS Volume Encryption Key Points
- Encryption is supported by all EBS volume types.
- Amazon EBS offers volume encryption capability.
- The volume key is encrypted under a KMS key in your account.
- Amazon EBS must have access to generate a volume key (VK) under a KMS key in the account. We must grant access permission for Amazon EBS to use the KMS key to create data keys and to encrypt and decrypt EBS Volumes.
- Amazon EBS can use AWS KMS with a "KMS key" to generate KMS encrypted volume keys. Cxs aren't required to build, maintain, and secure their own key management infrastructure.
- Amazon EBS does not support asymmetric encryption KMS keys.
Main Difference between Asymmetric and Symmetric Encryption Types here - EBS encrypts your volume with a data key using the industry-standard AES-256 XTS algorithm. Your data key is stored on disk with your encrypted data, but not before EBS encrypts it with your KMS key. Your data key never appears on disk in plaintext.The same data key is shared by snapshots of the volume and any subsequent volumes created from those snapshots if the volumes are encrypted using the same KMS key as the snapshot.
- We can manage(enable/disable) encryption by default and the default KMS key using API actions and CLI commands.
When will EBS Volume be encrypted and unencrypted during EBS Operations
When we create an encrypted EBS volume and attach it to a supported instance type, the following types of data are encrypted:
- Data at rest inside the volume
- All data moving between the volume and the instance
- All snapshots created from the encrypted volume
- All volumes/ami created from those snapshots
An AWSome picture representation of encrypted and unencrypted volumes during EBS Operations. Thanks to Matt Phillipy.
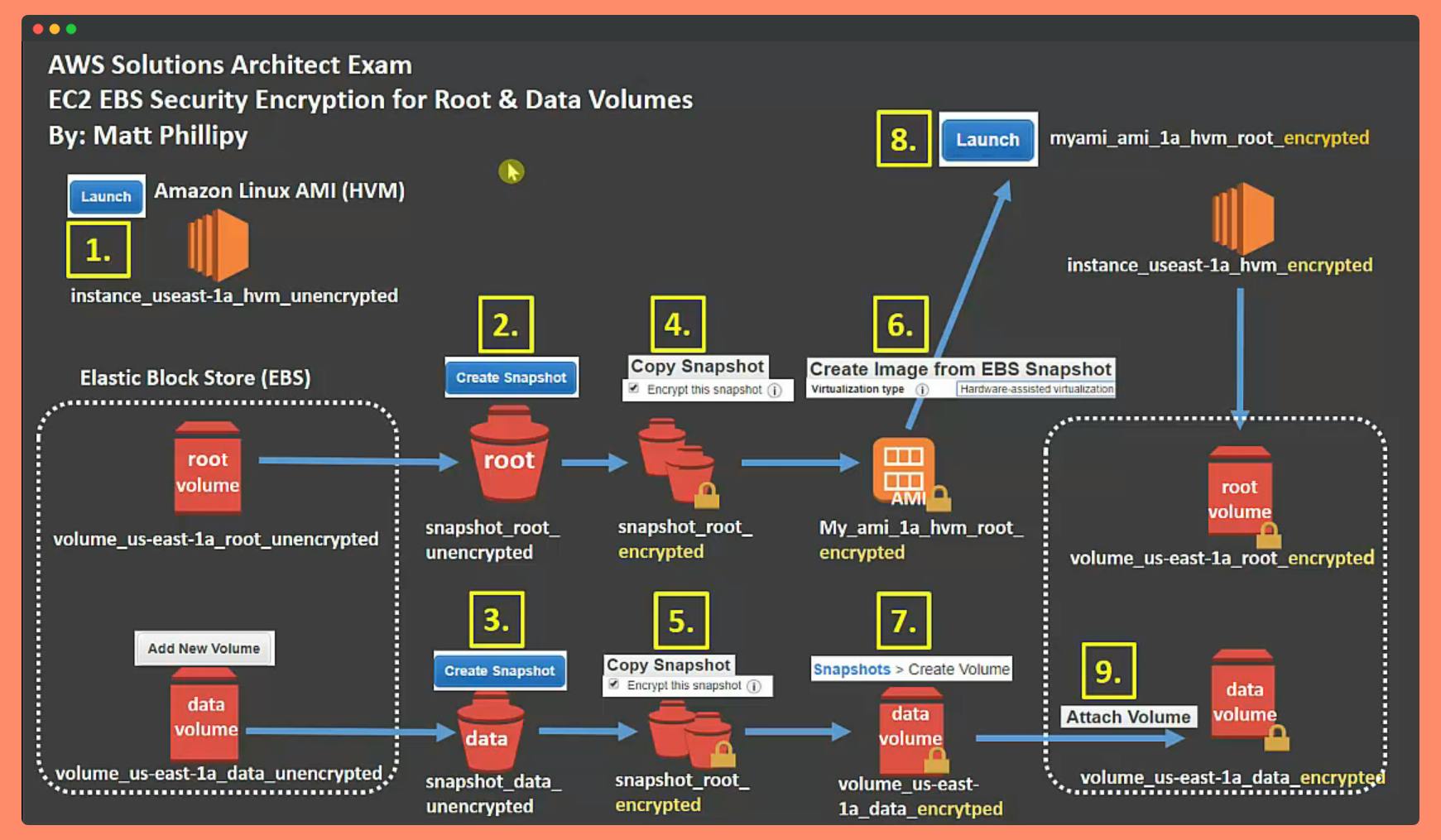
How-To Convert Unencrypted Volumes to Encrypted EBS Volumes
Step 1: On your EC2 instance with Volumes are UnEncrypted
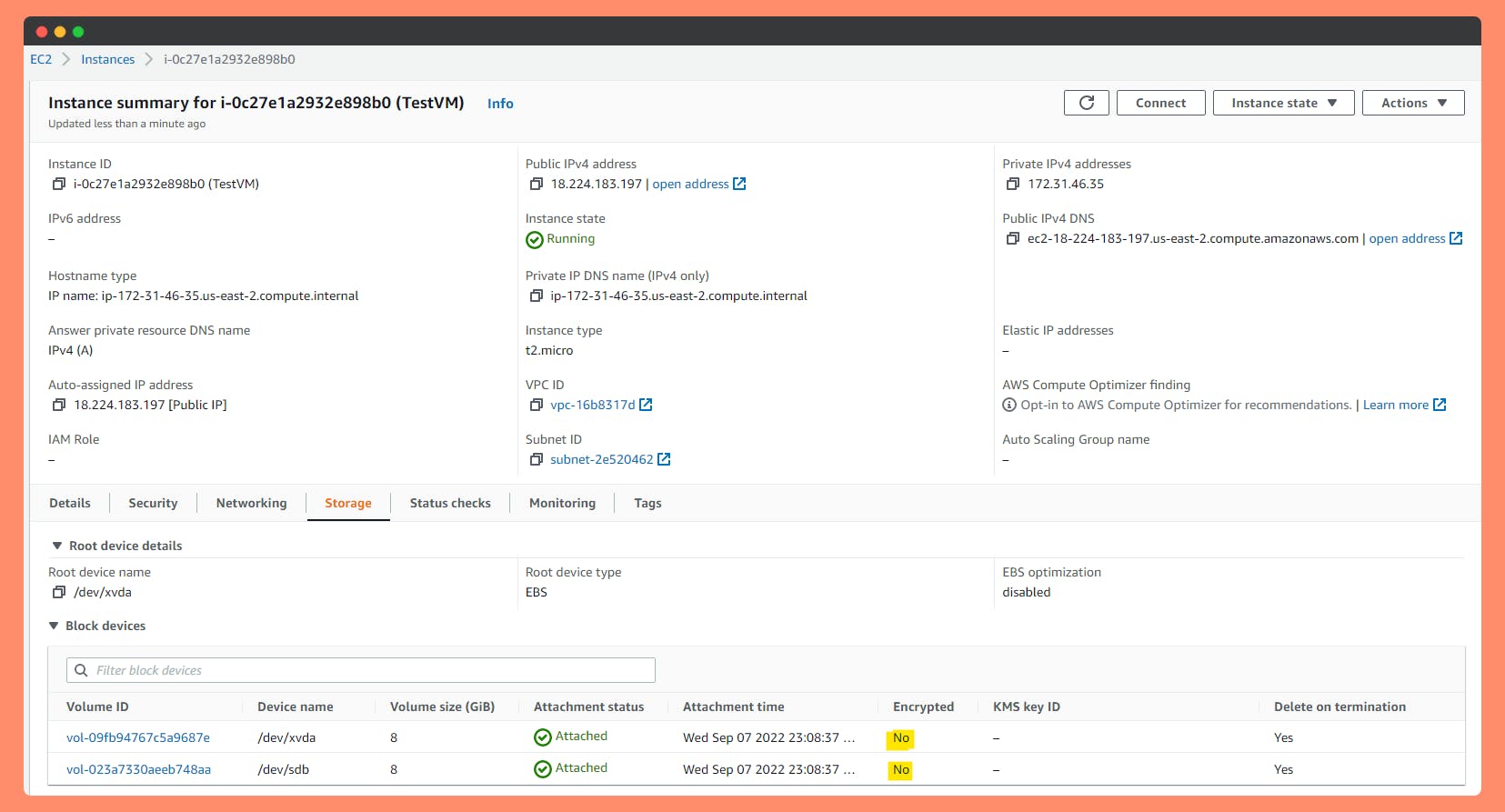 Step 2: Create a Snapshot from unencrypted volume.
Step 2: Create a Snapshot from unencrypted volume.
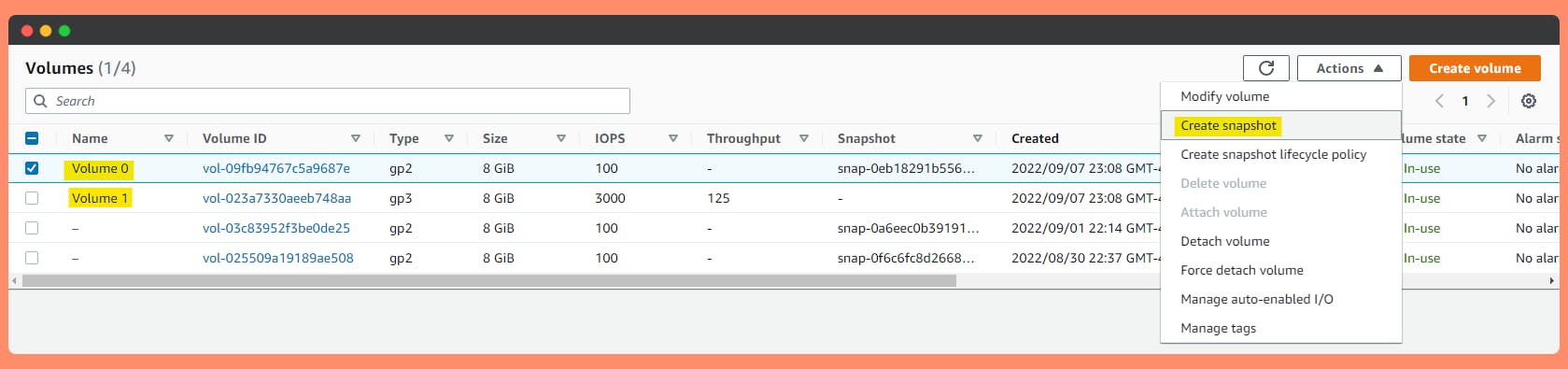 NOTE : It is not recommended to create Snapshot of Volume while data is being read/written on EBS storage. Reason being, While snapshot is getting created or during the creation, It would not have new data of Running EBS volume and drift will occur of data in the snapshot and new data. So better to Stop your EC2 instance before Converting Volume Encryption / snapshot operation.
NOTE : It is not recommended to create Snapshot of Volume while data is being read/written on EBS storage. Reason being, While snapshot is getting created or during the creation, It would not have new data of Running EBS volume and drift will occur of data in the snapshot and new data. So better to Stop your EC2 instance before Converting Volume Encryption / snapshot operation.
Step 3: Volume Snapshots will be unencrypted since it was created from unencrypted Volumes.
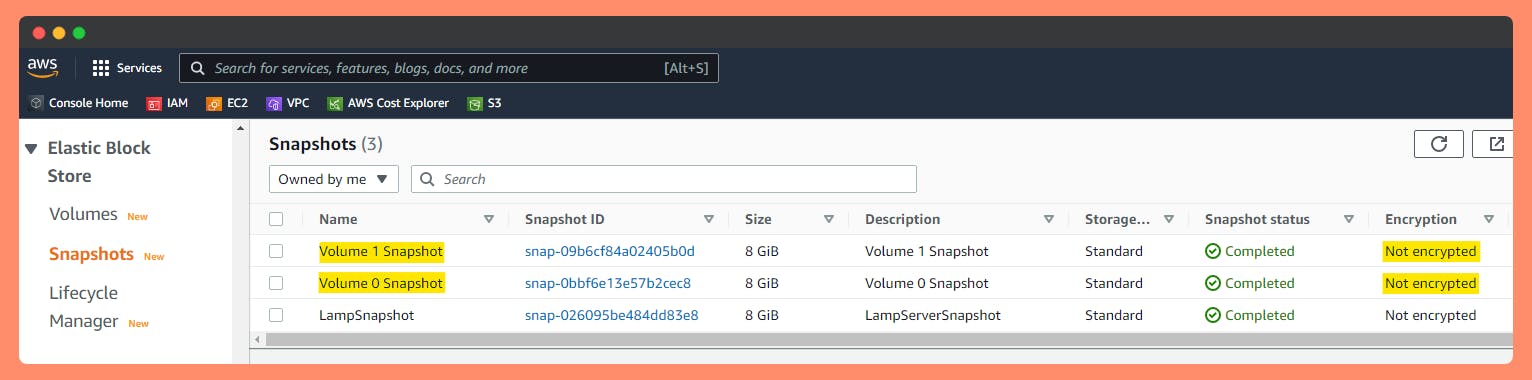 Step 4: Two Options.
Step 4: Two Options.
1st Option: Create Encrypted Volume from a Snapshot.
Note : No Option to change Region.
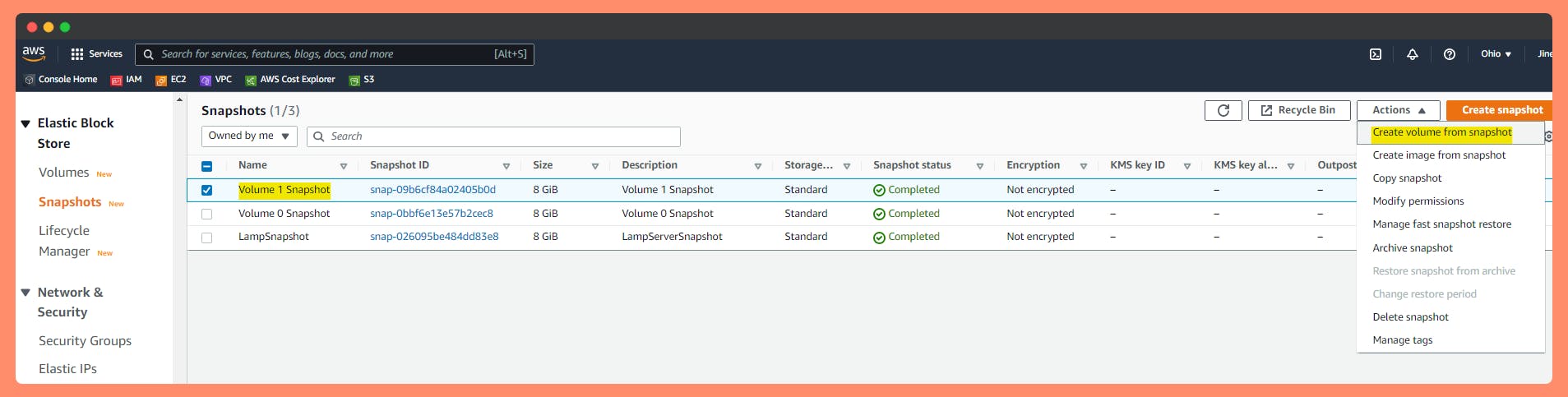
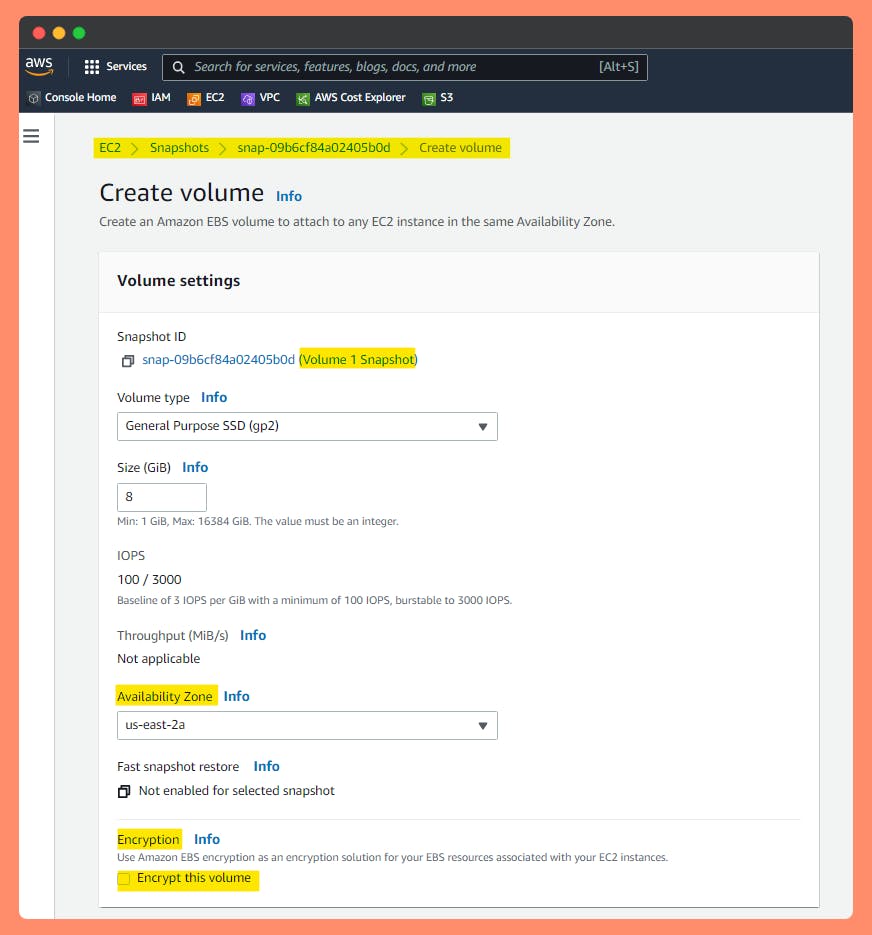
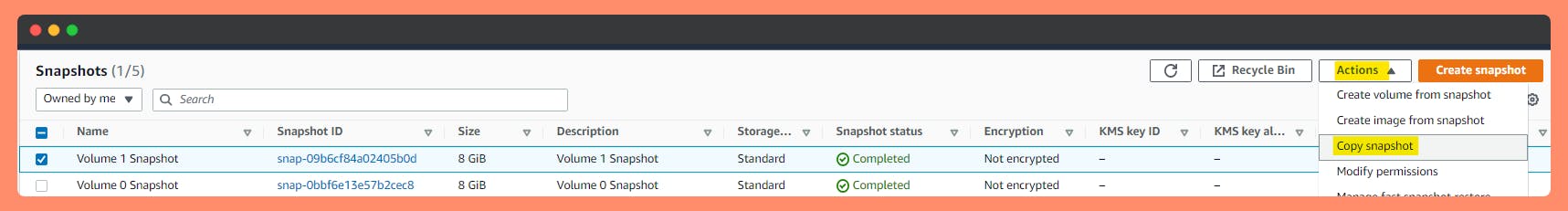
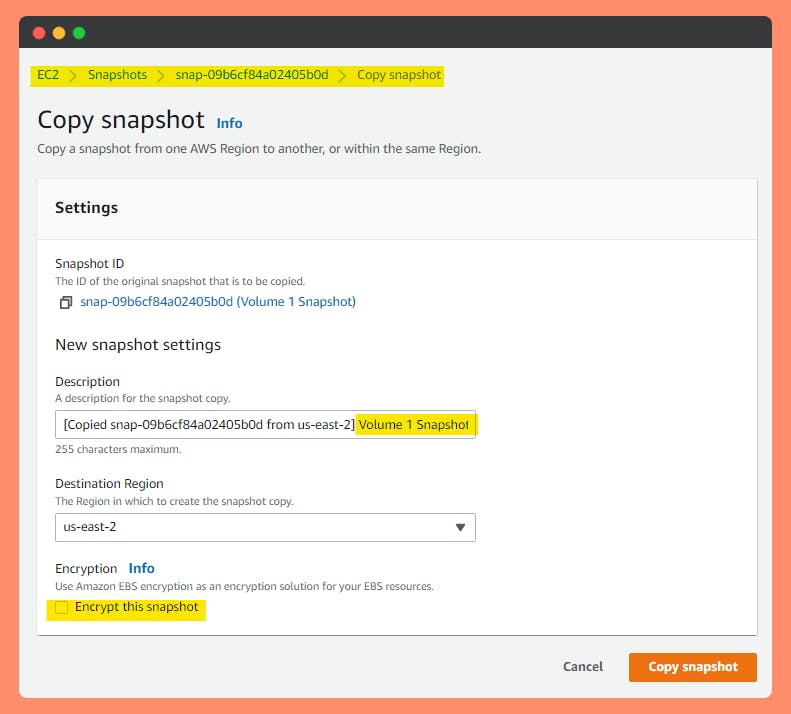
Copy unencrypted Volume snapshot to an encrypted Volume snapshot.
Note : Can change the Region of Copied Snapshot.
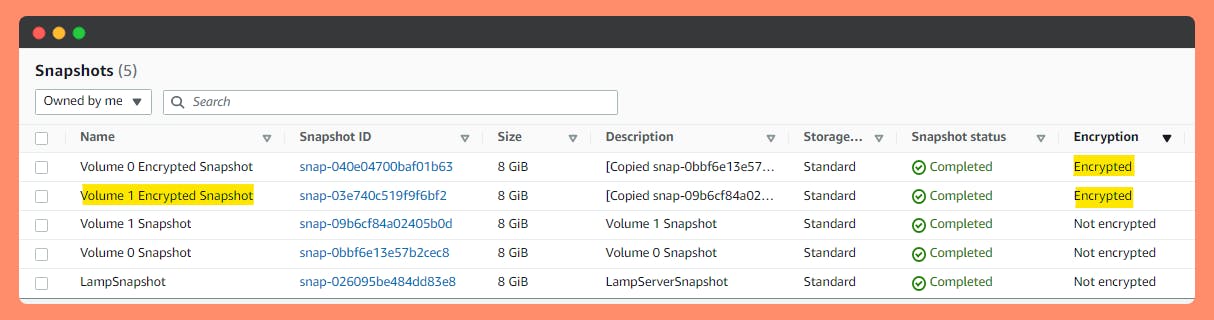
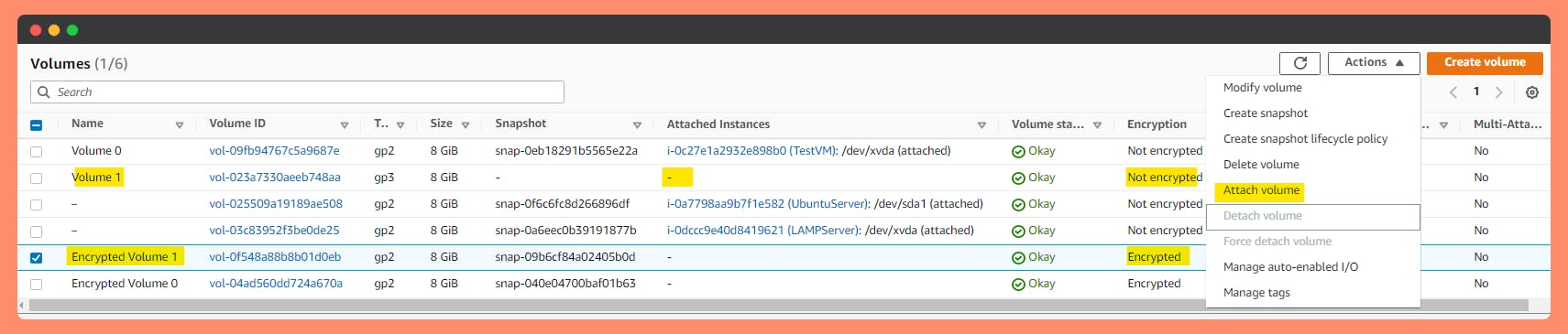
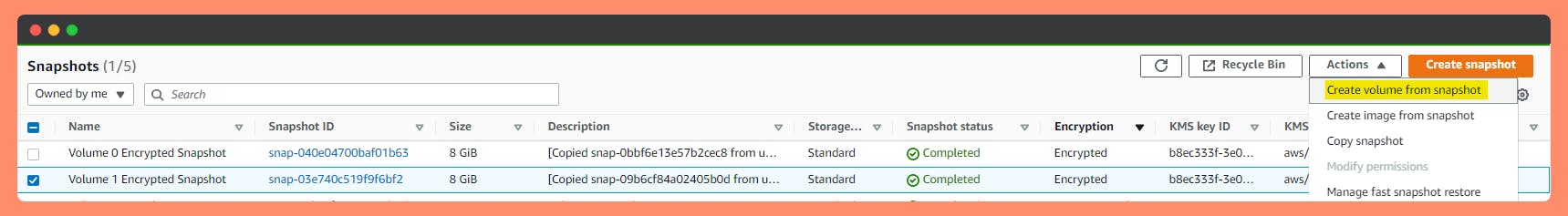 See all the Volumes attached and not attached to instances with encryption status. Go to Step 5
See all the Volumes attached and not attached to instances with encryption status. Go to Step 5
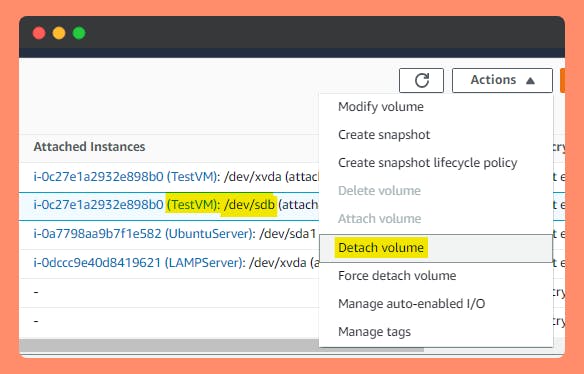
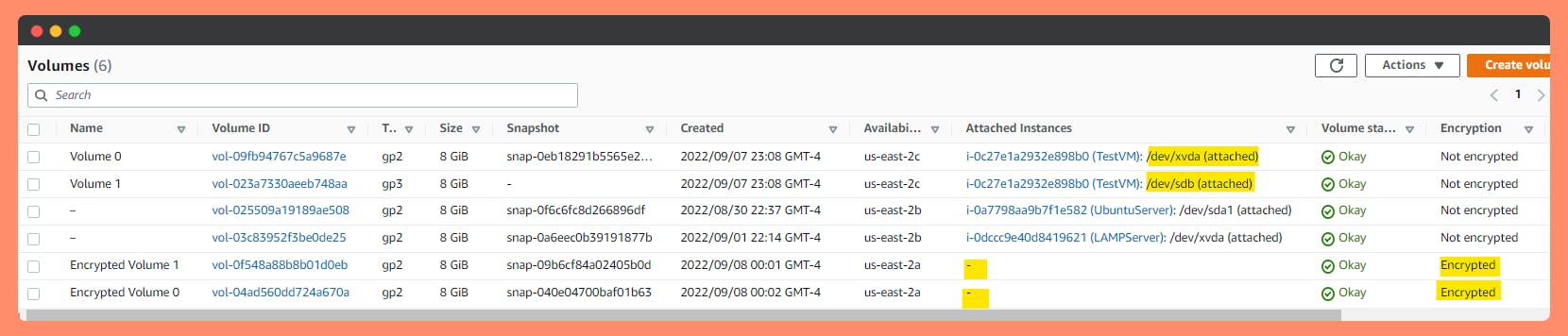 Step 5: Detach the original EBS volume and attach your new encrypted EBS volume, making sure to match the device name (/dev/xvda1, etc.)
Step 5: Detach the original EBS volume and attach your new encrypted EBS volume, making sure to match the device name (/dev/xvda1, etc.)
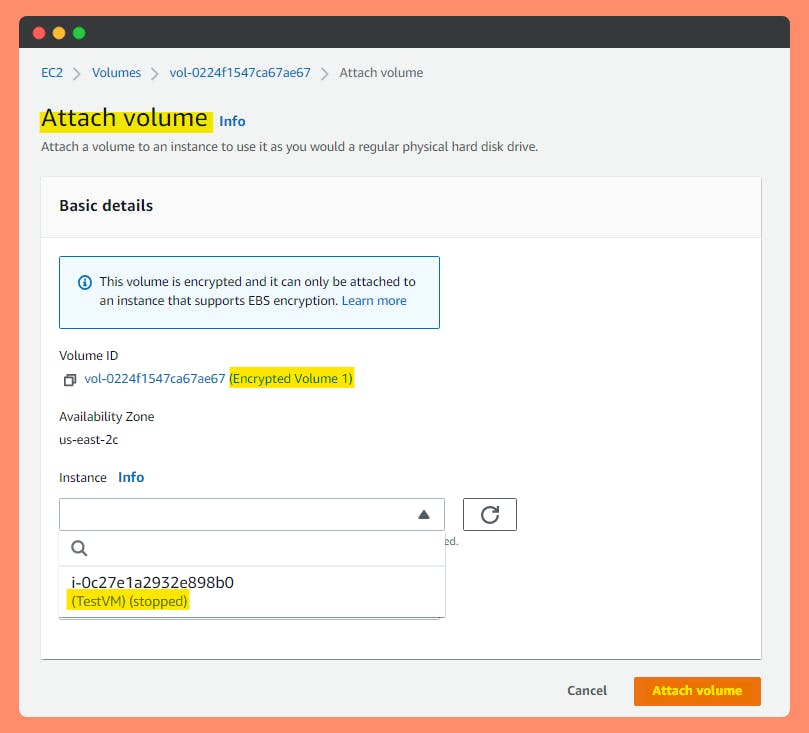 Successfully running "TestVM" with attached Encrypted Volumes.
Successfully running "TestVM" with attached Encrypted Volumes.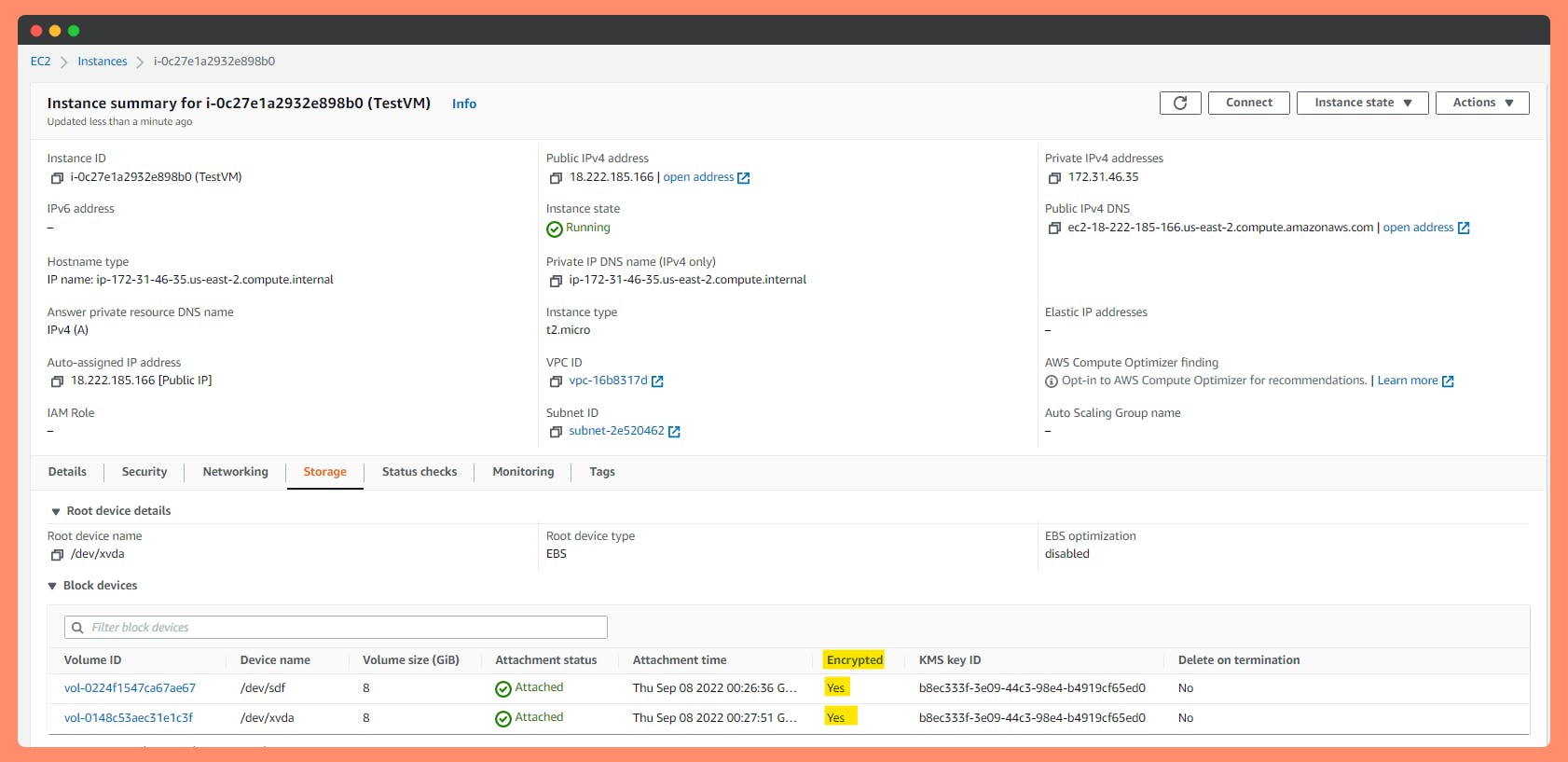
How-to TURN-ON automatic encryption of new Amazon EBS volumes and snapshot copies?
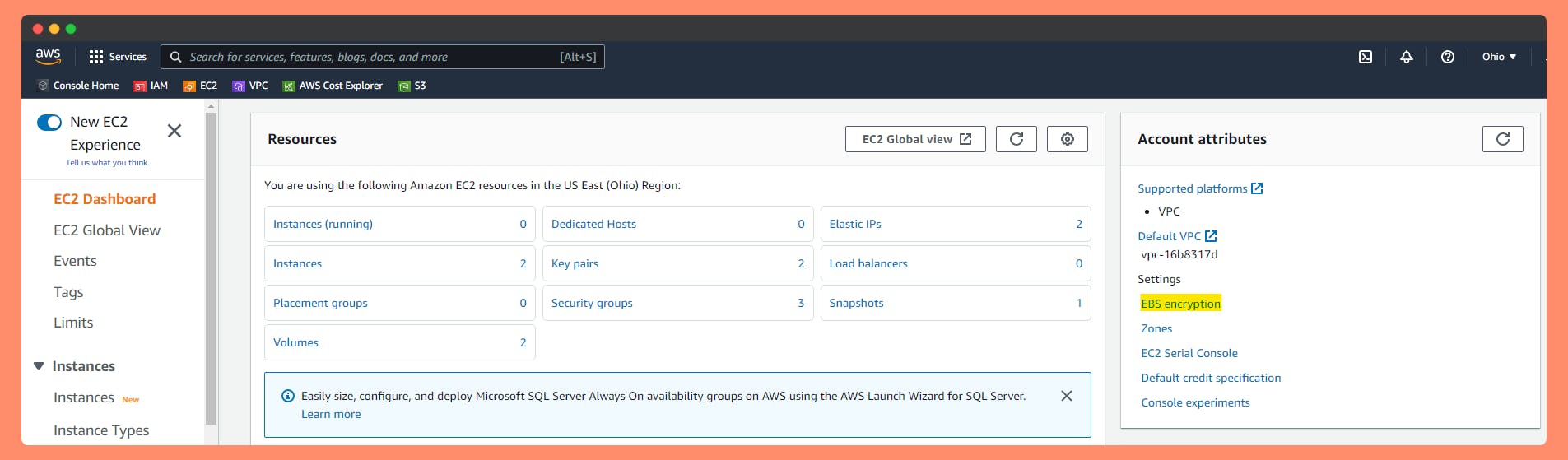
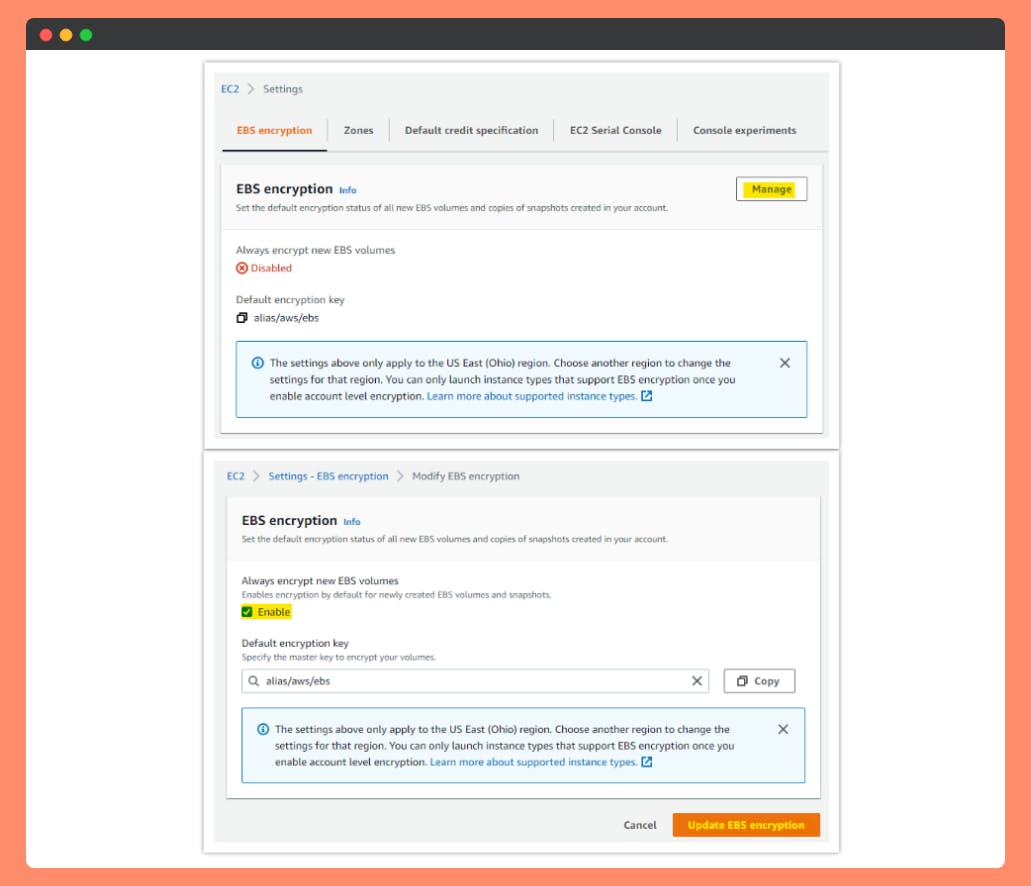
- Open the Amazon EC2 console.
- Select the Region from the drop-down menu.
- On the EC2 Dashboard, under Account Attributes, select Settings.
- Under EBS Storage, select Always encrypt new EBS volumes.
- Select Change the default key and choose any of your keys (default/CMKs) as the Default encryption key.
Select Save Settings by Update EBS Encryption.
Encryption scenarios
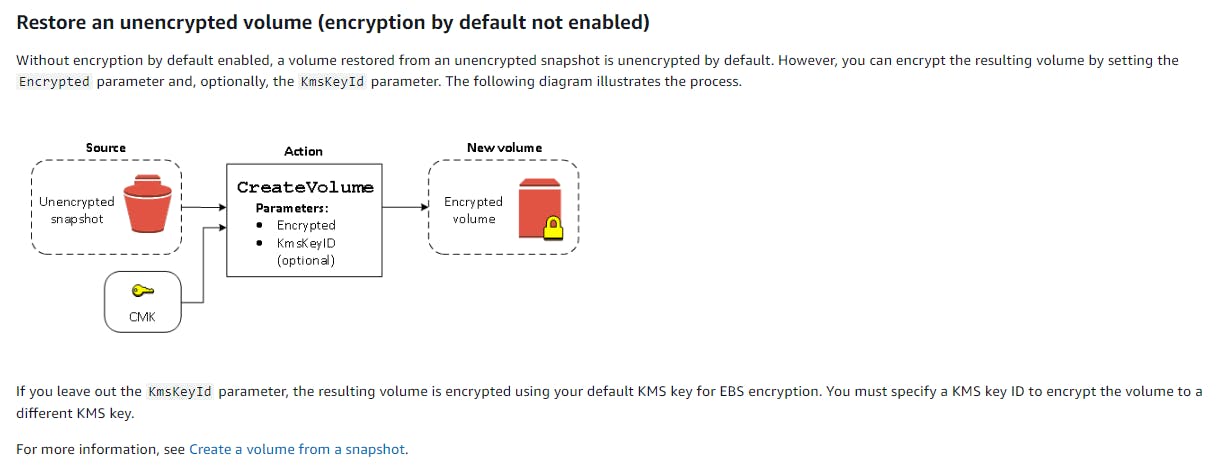
- Restore an unencrypted volume (encryption by default not enabled)
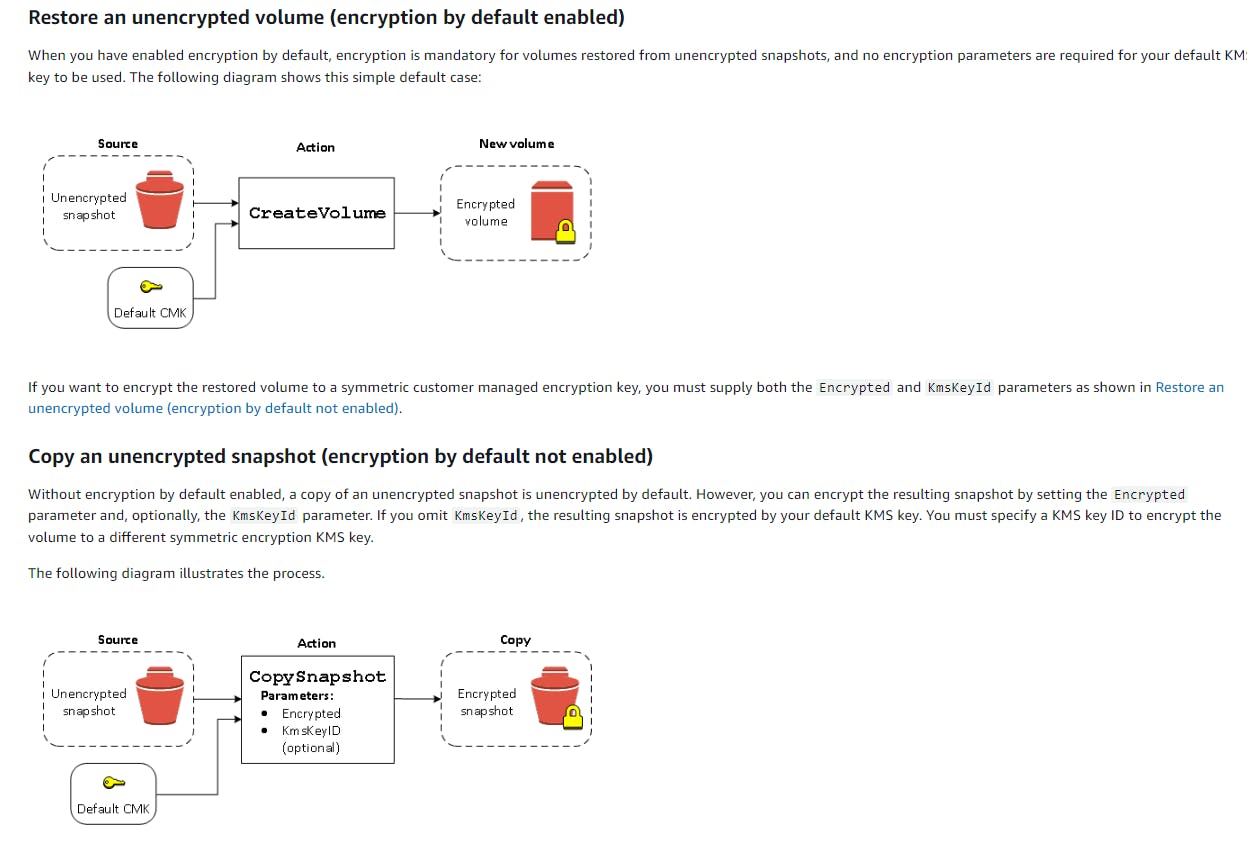
- Restore an unencrypted volume (encryption by default enabled)
- Copy an unencrypted snapshot (encryption by default not enabled)
- Copy an unencrypted snapshot (encryption by default enabled)
- Re-encrypt an encrypted volume
- Re-encrypt an encrypted snapshot
- Migrate data between encrypted and unencrypted volumes Encryption outcomes
- Encryption outcomes
More on that here
Thank you for reading and/or following along with the Blog.
Happy Learning.
Like and Follow for more Azure and AWS Content.
Regards,
Jineshkumar Patel

